Critical UNIX/Linux Printing Flaws Enable RCE, Malvertising Drives BlackCat Ransomware, 73 Firms Leaked with Manufacturing Hit Hardest, and CISA Adds SAP, Motion Spell, DrayTek, and D-Link Vulnerabilities
In our latest Cyber Intelligence Brief, Deepwatch ATI looks at new threats and techniques to deliver actionable intelligence for SecOps organizations.
Each week we look at in-house and industry threat intelligence and provide ATI analysis and perspective to shine a light on a spectrum of cyber threats.
Critical Flaws in UNIX/Linux Printing System Enable Remote Code Execution
The Rundown
On September 26, a security researcher published technical details for four vulnerabilities in the UNIX/Linux CUPS printing system that, when chained together, allow remote code execution. These flaws enable attackers to introduce a malicious printer by sending UDP datagrams to port 631 and, once a print job is initiated, execute arbitrary commands on the target system without authentication.
The technical impact of the vulnerabilities is serious. If UDP port 631 is accessible and the vulnerable service is listening, Linux, macOS, and other Unix-like systems are at risk of remote attacks. However, it is less likely that desktop machines/workstations running CUPS are exposed to the Internet in the same manner or in the same numbers that typical server editions of Linux would be. While proof-of-concept (POC) exploit code has been released, darkweb chatter notes that there are limitations that make exploitation less likely.
Source Material: Canonical and EvilSocket
Malvertising Fuels BlackCat Ransomware Attack
The Rundown
Attackers used Google ads to deliver Nitrogen malware to infiltrate an enterprise, which led to the deployment of Sliver, Cobalt Strike, Restic, and BlackCat ransomware in just eight days, a sophisticated strike revealed in The DFIR Reports’ latest report.
This attack underscores the threat of malvertising. It shows how cybercriminals can escalate from initial access to ransomware deployment, putting enterprise data and networks at grave risk while providing time for organizations to respond.
Source Material: The DFIR Report
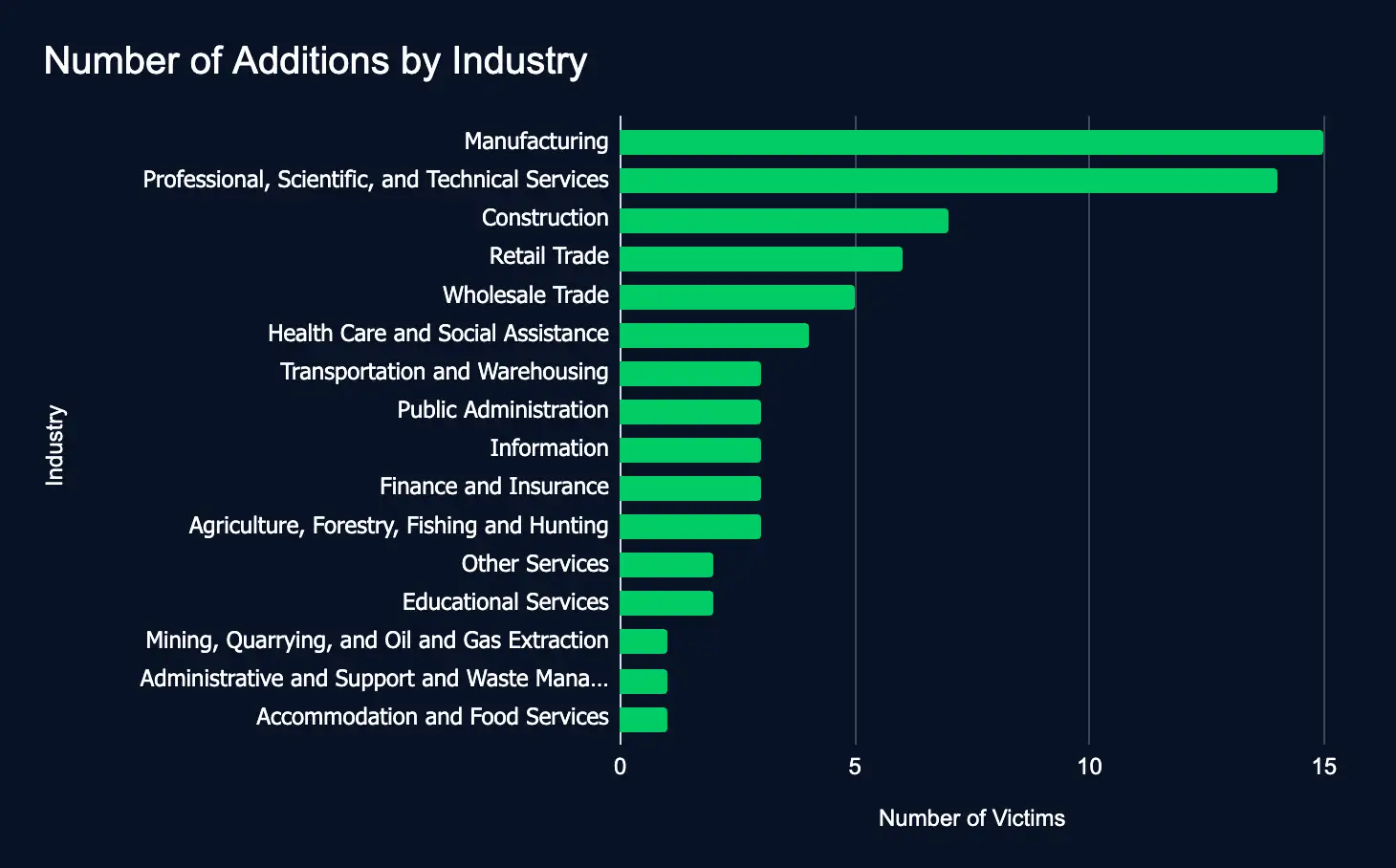
Leak Sites: 73 Firms Listed, Manufacturing Tops the List
The Rundown
In just one week, ransomware and data extortion leak sites added 73 new organizations, a decline from last week’s 131, spanning 21 countries and 16 industries. In the time frame, Play Ransomware led in new additions of all monitored leak sites.
The decline in data leak listings highlights ransomware attacks’ volatility and unpredictability. While this decline in activity may seem like a reprieve, the frequent fluctuation in listings demands attention, as no sector is immune.
CISA Adds Older SAP, Motion Spell, DrayTek, and D-Link Vulnerabilities to Exploited List
The Rundown
Four older vulnerabilities affecting SAP Commerce Cloud, Motion Spell GPAC, Multiple DrayTek Vigor Routers, and D-Link DIR-820 routers have been added to CISA’s Known Exploited Vulnerabilities catalog, urging immediate action to prevent potential system breaches and administrative takeover.
These newly added vulnerabilities highlight how critical it is to have a robust patch management program that addresses all applications and devices used. Failure to apply patches can have devastating consequences, even years later.
Recommendations
ATI recommends mitigative action occur according to the mitigation “Due Date” recommended by CISA.
Source Material: CISA
What We Mean When We Say
Estimates of Likelihood
We use probabilistic language to reflect the Intel Team’s estimates of the likelihood of developments or events because analytical judgments are not certain. Terms like “probably,” “likely,” “very likely,” and “almost certainly” denote a higher than even chance. The terms “unlikely” and “remote” imply that an event has a lower than even chance of occurring; they do not imply that it will not. Terms like “might” reflect situations where we are unable to assess the likelihood, usually due to a lack of relevant information, which is sketchy or fragmented. Terms like “we can’t dismiss,” “we can’t rule out,” and “we can’t discount” refer to an unlikely, improbable, or distant event with significant consequences.
Confidence in Assessments
Our assessments and projections are based on data that varies in scope, quality, and source. As a result, we assign our assessments high, moderate, or low levels of confidence, as follows:
High confidence indicates that our decisions are based on reliable information and/or that the nature of the problem allows us to make a sound decision. However, a “high confidence” judgment is not a fact or a guarantee, and it still carries the risk of being incorrect.
Moderate confidence denotes that the information is credible and plausible, but not of high enough quality or sufficiently corroborated to warrant a higher level of assurance.
Low confidence indicates that the information’s credibility and/or plausibility are in doubt, that the information is too fragmented or poorly corroborated to make solid analytic inferences, or that we have serious concerns or problems with the sources.

Share