Earth Lusca Unveils KTLVdoor Backdoor, Russia’s GRU Cyber Unit Exposed, 60 Firms Leaked with Manufacturing Hit Hardest, and CISA Adds Microsoft, ImageMagick, Linux, and SonicWall Vulnerabilities
In our latest Cyber Intelligence Brief, Deepwatch ATI looks at new threats and techniques to deliver actionable intelligence for SecOps organizations.
Each week we look at in-house and industry threat intelligence and provide ATI analysis and perspective to shine a light on a spectrum of cyber threats.
Earth Lusca’s New Backdoor, KTLVdoor
The Rundown
Earth Lusca, an advanced persistent threat (APT) group, is leveraging a new unreported malware variant, KTLVdoor, in its cyber-espionage operations.
The introduction of KTLVdoor by Earth Lusca is a significant escalation in cyber espionage tactics. Due to its advanced stealth capabilities and potential for data breaches and more sophisticated attacks, KTLVdoor poses heightened risks to organizations.
Source Material: Trend Micro
Cyber Threat of Russia’s GRU Direct Action Unit Exposed
The Rundown
A Russian GRU unit known for its direct action operations, like coups and assassinations, is now known to have an offensive cyber operation team. The unit has been targeting global infrastructure, posing a direct threat to organizations since 2020.
Unit 29155 isn’t just another threat group; they’re a military-grade operation using cyberattacks to destabilize governments, disrupt critical infrastructure, and target aid efforts, raising the stakes for global security.
Source Material: CISA
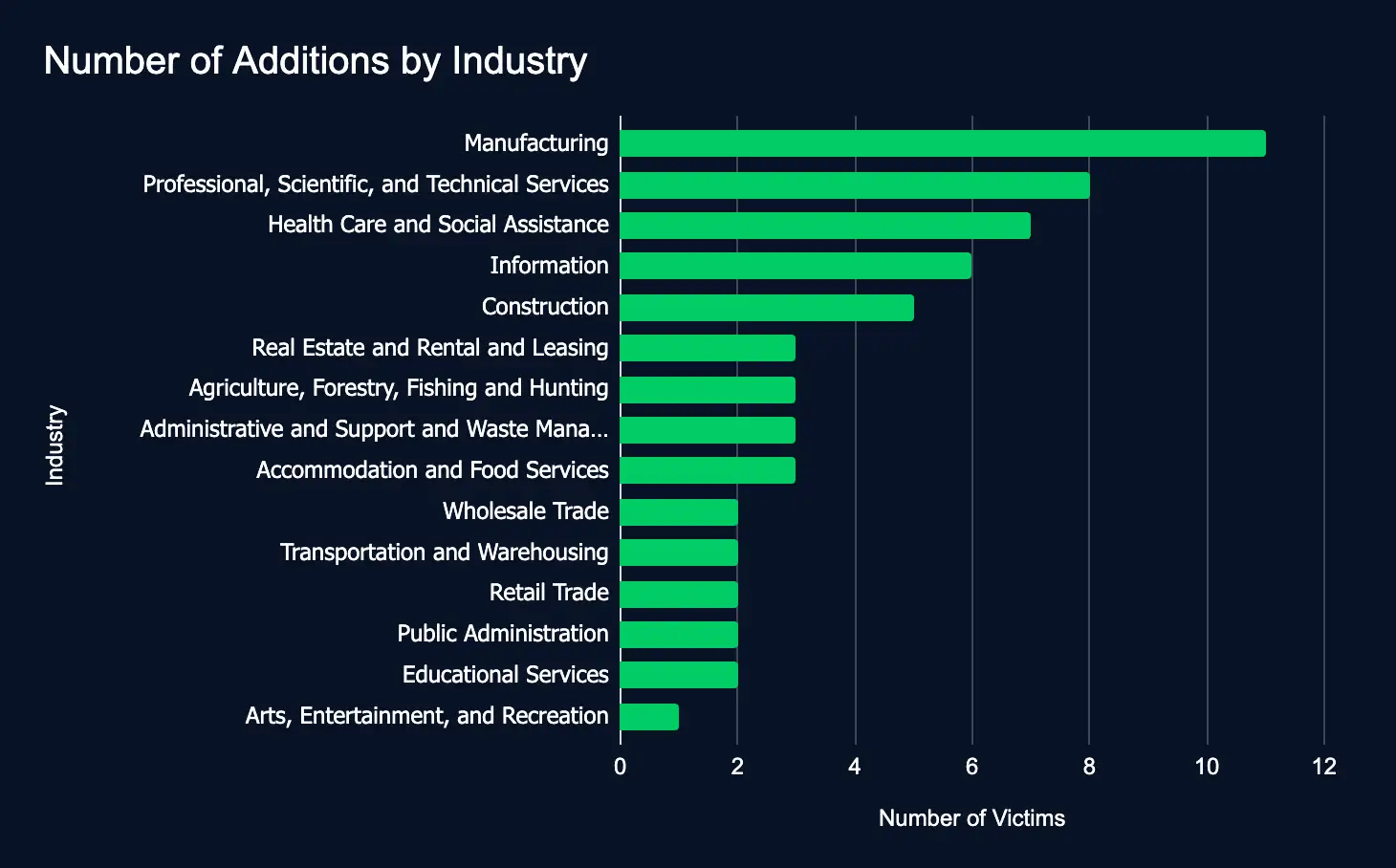
60 Firms Listed on Data Leak Sites in a Week: Manufacturing Tops the List
The Rundown
Between September 2 and 8, 2024, 60 new organizations were listed on ransomware and data extortion leak sites. The listed organizations on these leak sites span 15 industries, from the United States to Belgium.
These new additions underscore key sectors’ increasing vulnerability, such as manufacturing, healthcare, and professional services. The global spread of ransomware and data extortion attacks demands urgent attention to cybersecurity, as industries worldwide face rising threats to sensitive data and operational integrity.
CISA Adds Microsoft, ImageMagick, Linux, and SonicWall Vulnerabilities to Exploited List
The Rundown
The Cybersecurity and Infrastructure Security Agency (CISA) has added seven vulnerabilities affecting Microsoft, Linux, ImageMagick, and SonicWall products to its catalog of known exploited vulnerabilities, warning of potential threats if these are left unpatched.
These vulnerabilities target widely used systems across industries. If not addressed, they pose significant risks to data integrity and network security, potentially allowing attackers to bypass critical defenses or gain unauthorized access. Organizations must act and apply the necessary updates and mitigations before the recommended deadlines.
Recommendations
ATI recommends mitigative action occur according to the mitigation “Due Date” recommended by CISA.
Source Material: CISA
What We Mean When We Say
Estimates of Likelihood
We use probabilistic language to reflect the Intel Team’s estimates of the likelihood of developments or events because analytical judgments are not certain. Terms like “probably,” “likely,” “very likely,” and “almost certainly” denote a higher than even chance. The terms “unlikely” and “remote” imply that an event has a lower than even chance of occurring; they do not imply that it will not. Terms like “might” reflect situations where we are unable to assess the likelihood, usually due to a lack of relevant information, which is sketchy or fragmented. Terms like “we can’t dismiss,” “we can’t rule out,” and “we can’t discount” refer to an unlikely, improbable, or distant event with significant consequences.
Confidence in Assessments
Our assessments and projections are based on data that varies in scope, quality, and source. As a result, we assign our assessments high, moderate, or low levels of confidence, as follows:
High confidence indicates that our decisions are based on reliable information and/or that the nature of the problem allows us to make a sound decision. However, a “high confidence” judgment is not a fact or a guarantee, and it still carries the risk of being incorrect.
Moderate confidence denotes that the information is credible and plausible, but not of high enough quality or sufficiently corroborated to warrant a higher level of assurance.
Low confidence indicates that the information’s credibility and/or plausibility are in doubt, that the information is too fragmented or poorly corroborated to make solid analytic inferences, or that we have serious concerns or problems with the sources.

Share