Shadow IT Risks Exposed in Server Compromise, Vice Society Targets Healthcare with INC Ransomware, 131 Firms Leaked Amid CL0P’s Surge, and CISA Adds New Ivanti Vulnerabilities
In our latest Cyber Intelligence Brief, Deepwatch ATI looks at new threats and techniques to deliver actionable intelligence for SecOps organizations.
Each week we look at in-house and industry threat intelligence and provide ATI analysis and perspective to shine a light on a spectrum of cyber threats.
Unmonitored Server Compromise Demonstrates the Risk of Shadow IT in Secure Networks
The Rundown
In March 2024, a China-nexus threat actor compromised an unmanaged AIX server using default credentials, launching an attack that bypassed network defenses and exposed sensitive credentials.
Unmonitored systems like shadow IT environments are prime targets for attackers, putting entire networks at risk despite robust security measures elsewhere. This incident reveals how even obscure, unmanaged servers can be leveraged to compromise secure environments.
Source Material: Binary Defense
Vice Society Targets Healthcare with New Backdoor and INC Ransomware
The Rundown
For the first time, the notorious Vice Society has launched INC ransomware attacks against U.S. healthcare organizations, gaining initial access through Gootloader infections and deploying a new backdoor, dubbed Supper, signifying a change in their tactics and techniques.
This shift in Vice Society’s tactics and techniques signals an increasing threat to the healthcare sector, risking patient data, financial losses, and operational disruptions as ransomware attacks evolve.
Source Material: Microsoft
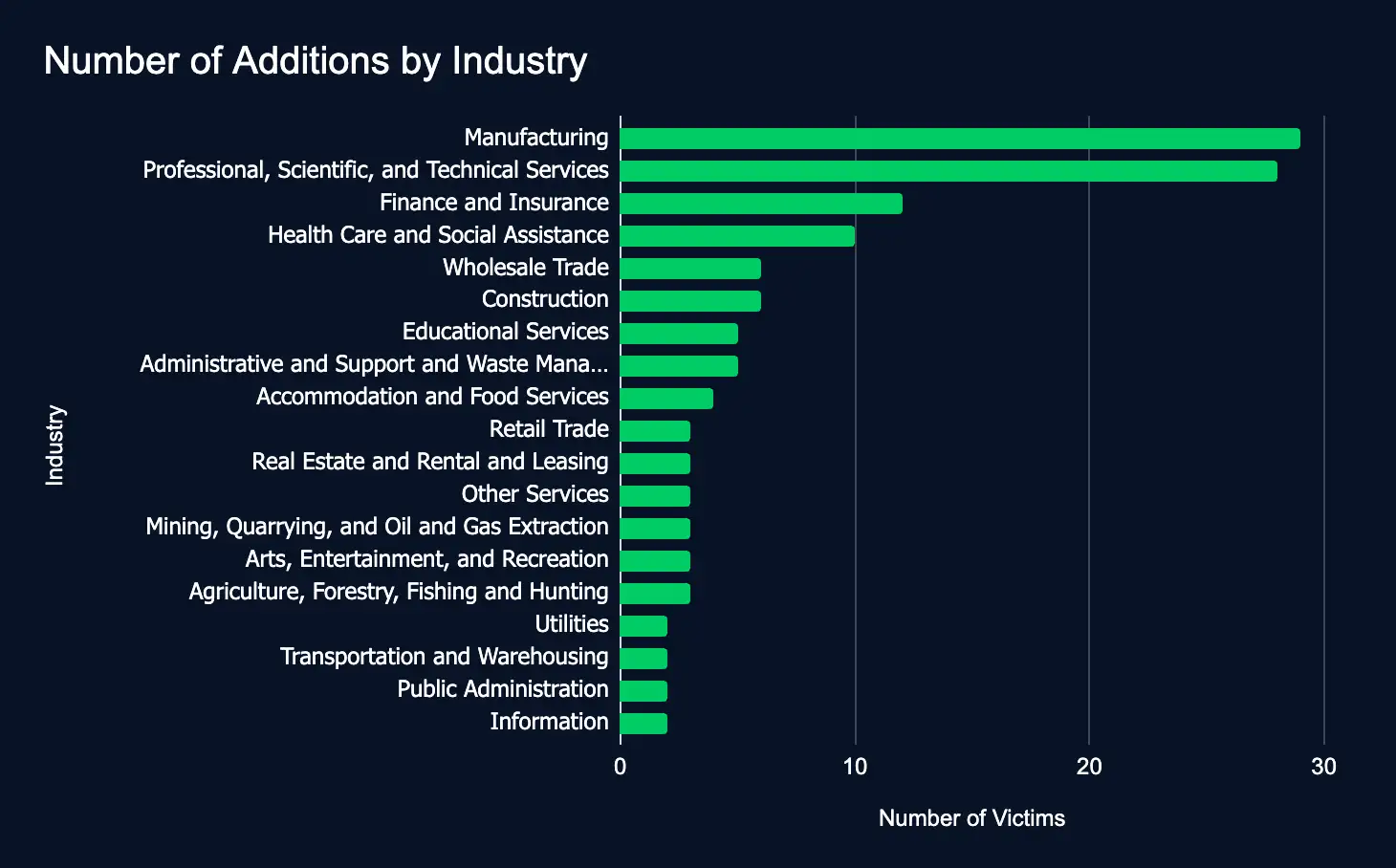
131 Firms Listed on Data Leak Sites in a Week: CL0P Most Active Period of 2024
The Rundown
Ransomware and data extortion leak sites added 131 new victims from 28 countries, spanning 19 industries, in just one week, with CL0P leading the surge, marking its most active period of 2024.
The sheer volume of data leak listings—131 organizations in a single week—highlights the relentless pace of ransomware threats, forcing businesses across various industries to confront the growing risk of being targeted. This surge in activity demands attention as no sector appears immune.
CISA Adds 2 Ivanti Vulnerabilities to Exploited List
The Rundown
Two vulnerabilities impacting two Ivanti products, Cloud Services Appliance (CSA) and Virtual Traffic Manager, have been added to CISA’s Known Exploited Vulnerabilities catalog, urging immediate action to prevent potential system breaches and administrative takeover.
These vulnerabilities expose Ivanti users to severe risks, including unauthorized access and control of key systems. With Ivanti CSA reaching end-of-life and unpatched versions vulnerable, swift mitigation is crucial to avoid exploitation and potential ransomware attacks.
Recommendations
ATI recommends mitigative action occur according to the mitigation “Due Date” recommended by CISA.
Source Material: CISA
What We Mean When We Say
Estimates of Likelihood
We use probabilistic language to reflect the Intel Team’s estimates of the likelihood of developments or events because analytical judgments are not certain. Terms like “probably,” “likely,” “very likely,” and “almost certainly” denote a higher than even chance. The terms “unlikely” and “remote” imply that an event has a lower than even chance of occurring; they do not imply that it will not. Terms like “might” reflect situations where we are unable to assess the likelihood, usually due to a lack of relevant information, which is sketchy or fragmented. Terms like “we can’t dismiss,” “we can’t rule out,” and “we can’t discount” refer to an unlikely, improbable, or distant event with significant consequences.
Confidence in Assessments
Our assessments and projections are based on data that varies in scope, quality, and source. As a result, we assign our assessments high, moderate, or low levels of confidence, as follows:
High confidence indicates that our decisions are based on reliable information and/or that the nature of the problem allows us to make a sound decision. However, a “high confidence” judgment is not a fact or a guarantee, and it still carries the risk of being incorrect.
Moderate confidence denotes that the information is credible and plausible, but not of high enough quality or sufficiently corroborated to warrant a higher level of assurance.
Low confidence indicates that the information’s credibility and/or plausibility are in doubt, that the information is too fragmented or poorly corroborated to make solid analytic inferences, or that we have serious concerns or problems with the sources.

Share