Knight Ransomware Jousts, Sandman Creeps, APTs Work Together on Cyber Espionage, Cozy Bear Evolves, and New RaaS ShadowSyndicate Steps Out
Threat actors deliver Knight ransomware in phishing emails, Sandman APT targets global telecoms in a cyber-espionage campaign, three APTs seem to have coordinated efforts in cyber espionage against a Southeast Asian government, Cozy bear is improving its malware and delivery methods–all of this plus the latest from data leak sites and 4 new CVEs.
In our latest Cyber Intelligence Brief, Deepwatch ATI looks at new threats and techniques to deliver actionable intelligence for SecOps organizations.
As a leading managed security platform, Deepwatch stands at the forefront of delivering actionable intelligence to keep pace with the ever-evolving threat landscape. Through the Deepwatch Adversary Tactics and Intelligence (ATI) team, we arm your organization with essential knowledge, giving you the power to proactively spot and neutralize risks, amplify your security protocols, and shield your financial stability.
Each week we look at in-house and industry threat intelligence and provide ATI analysis and perspective to shine a light on a spectrum of cyber threats.
This Week’s Source Material
- Proofpoint: The Return of Direct Ransomware Delivery?
- SentinelOne: Sandman APT | A Mystery Group Targeting Telcos with a LuaJIT Toolkit
- Palo Alto Unit 42:
- Researchers Discover Multiple Espionage Operations Targeting Southeast Asian Government
- Cyberespionage Attacks Against Southeast Asian Government Linked to Stately Taurus, Aka Mustang Panda
- Persistent Attempts at Cyberespionage Against Southeast Asian Government Target Have Links to Alloy Taurus
- Rare Backdoors Suspected to be Tied to Gelsemium APT Found in Targeted Attack in Southeast Asian Government
- Mandiant: Backchannel Diplomacy: APT29’s Rapidly Evolving Diplomatic Phishing Operations
- Group I-B: Dusting for fingerprints: ShadowSyndicate, a new RaaS player?
- The Latest Additions from Data Leak Sites
- CISA Adds 4 CVEs to its Known Exploited Vulnerabilities Catalog
Threat Actors Deliver Knight Ransomware in Phishing Emails
Knight Ransomware – Phishing – No Data Exfiltration – Industries/All
Overview & Background
In a recent blog post from Proofpoint titled “The Return of Direct Ransomware Delivery?” details the resurgence of direct email delivery of Knight ransomware, highlighting several campaigns observed in August 2023. The blog post aims to shed light on the tactics, techniques, and procedures (TTPs) employed by the threat actors behind Knight ransomware and to provide insights into the evolving threat landscape. The blog post analyzes the characteristics of the email campaigns, the modifications in the attack chain, and the behavior of the ransomware upon installation, focusing on its lateral movement and encryption methods.
According to SentinelOne, “Knight ransomware emerged in August of 2023 as an evolution or rebrand of Cyclops ransomware. Knight ransomware operates as a multi-extortion group, hosting a TOR-based blog to list victim names and any exfiltrated data. Victims are aggressively coerced into payment to avoid having their data leaked publicly. Knight has been actively advertised and sold on the RAMP forum. Knight ransomware is delivered primarily through phishing and spear phishing campaigns. Some early examples include those masquerading as messages from TripAdvisor.” Knight developers also offer affiliates a lite version, or “Knight Lite,” for broader, non-targeted spam-based attacks.
Threat Analysis
The threat actors behind Knight ransomware employ a multifaceted approach to deliver the malicious payload via email. The email campaigns observed were predominantly low volume, with fewer than 500 messages, although one contained over 1,000. These campaigns primarily targeted English-speaking users, with additional campaigns in Italian and German. The emails had lures themed around invoices and messages from well-known travel websites, predominantly targeting hospitality organizations. When opened, these lures contained an HTML attachment that loaded a browser-in-the-browser interface spoofing legitimate sites, prompting victims to download a zipped executable or XLL file containing the ransomware. Later, campaigns modified the attack chain to include an interstitial zip file containing either an LNK linking to a WebDAV share or an XLL. Both installed a downloader that then deployed the Knight payload. Once installed, the ransomware initiated lateral movement, scanning for private IP addresses before encrypting networked devices.
The intentions of the threat actors behind Knight ransomware are financial gain, as evidenced by the ransom demands ranging from $5,000-$15,000 in Bitcoin. The ransomware encrypts files and leaves a ransom note with no current indication of data exfiltration. The lack of data exfiltration suggests that the actors do not seek to sell the data in underground marketplaces or will extort victims by threatening to release the data. The objectives of these actors are to target a variety of users, focusing on English-speaking, aiming for unauthorized access and disruption of systems through encryption. The capabilities of the threat actors are evident in their ability to modify attack chains, utilize different lures, and develop new downloaders, indicating a level of adaptability and resourcefulness in their operations.
Risk & Impact Assessment
The risk posed by Knight ransomware is significant, given its direct email delivery method and affiliates’ ability to adapt and modify attack chains. There is a low to moderate risk of organizations being affected by Knight Ransomware, giving organizations time to implement necessary mitigations to prevent an attack. The threat jeopardizes the availability of data and information systems, enabling threat actors to disrupt operations and encrypt critical data. The absence of data exfiltration does not diminish the risk and impact; it only takes one user to open the attachment, impacting the organization. Knight ransomware can have a substantial material impact on affected organizations. This impact can manifest through various means, including operational disruption, reputation damage, ransom payments, regulatory fines, remediation costs, and business downtime, potentially affecting net sales, revenues, and operational continuity. The ransom demands further exacerbate the financial implications, highlighting the tangible consequences of the threat actor’s operations on organizational assets and functions.
Sandman APT Targets Global Telecoms in August Cyber-Espionage Campaign
Sandman – LuaDream – Pass-the-Hash – DLL Sideloading – Data Exfiltration – Information
Overview & Background
A blog post from SentinelOne titled “Sandman APT | A Mystery Group Targeting Telcos with a LuaJIT Toolkit” details the activities of an advanced persistent threat (APT) group dubbed Sandman conducted in August 2023, which primarily targeted telecommunication providers across the Middle East, Western Europe, and the South Asian subcontinent. The blog post aims to shed light on Sandman’s deployment of a novel modular backdoor utilizing the LuaJIT platform, referred to as LuaDream, and to analyze the group’s tactics, techniques, and procedures (TTPs). The blog post explores the implementation and architecture of LuaDream, the strategic lateral movements and minimal engagements of the threat actor, and the geographical distribution of the victims.
Sandman is an enigmatic APT group of unknown origin, characterized by its strategic and deliberate approach to minimize detection. Given these providers’ sensitive data, the group has focused on targeting telecommunications providers, likely for espionage motivations. LuaJIT, or Lua Just-In-Time Compiler, is a lightweight, high-performance scripting language often used in gaming and embedded applications. It is relatively rare in the context of APT malware, making its use by Sandman notable. The LuaJIT platform allows for the execution of malicious Lua script code, which can be challenging to detect, indicating a well-executed and actively developed project by Sandman.
Threat Analysis
The group employed strategic lateral movements and minimal engagements to achieve its objectives while minimizing the risk of detection. The activities observed suggested a deliberate approach, with the group infiltrating specifically targeted workstations and deploying the necessary folders and files for loading and executing LuaDream, refraining from any further actions that might trigger alarms.
In the initial stages of their campaign, Sandman exhibited adeptness in utilizing various infiltration techniques. The group leveraged the pass-the-hash technique over the NTLM authentication protocol to gain unauthorized access, highlighting their ability to abuse authentication mechanisms. Additionally, the theft of administrative credentials was a pivotal step in their strategy, enabling them to maneuver through the targeted networks with elevated privileges. This approach facilitated the deployment of LuaDream through DLL hijacking, allowing them to execute malicious code by exploiting the loading of legitimate DLLs. These tactics underscored Sandman’s meticulous planning and execution, revealing their proficiency in utilizing techniques to compromise systems and maintain persistence.
LuaDream, a novel modular backdoor developed using the LuaJIT platform, stood as the centerpiece of Sandman’s arsenal. SentinelOne could not associate LuaDream with any known threat actor at the time of publication. However, they lean towards the possibility of a private contractor or mercenary group. The backdoor is characterized by its multi-component and multi-protocol nature, with the main functionalities revolving around managing actor-provided plugins and exfiltrating system and user information. The architecture of LuaDream indicated an actively maintained and developed project of considerable scale, with the implementation designed to evade detection and hinder analysis. The backdoor employed intricate staging processes, conducted entirely in memory, involving a combination of fully-formed DLL PE images, code, and LuaJIT bytecode. LuaDream communicated over various protocols, including TCP, HTTPS, WebSocket, and QUIC, showcasing its versatility in establishing connections with command and control (C2) servers.
The primary targets of Sandman’s campaign were telecommunications providers in the Middle East, Western Europe, and the South Asian subcontinent. The group’s focus on this sector suggested a strategic interest in accessing sensitive data, a common target for intelligence collection activities. The geographical distribution of the victims indicated a broad and diversified targeting approach, hinting at the group’s extensive capabilities and resources.
The threat actors’ intentions behind these operations appeared to be intelligence collection due to the strategic targeting of telecommunication providers and the deployment of advanced malware like LuaDream. The group aimed to gather sensitive information, likely for political, economic, or strategic advantage. The sophistication of the attacks and the targets indicated objectives related to unauthorized access to systems holding valuable information to exfiltrate sensitive data. The capabilities of Sandman, as evidenced by the development and deployment of LuaDream, demonstrated a high level of technical proficiency, resourcefulness, and adaptability, marking them as a significant threat in the cyber landscape.
Risk & Impact Assessment
Given Sandman’s known operations and focus on intelligence collection, the discernible risk to customers predominantly pertains to losing confidentiality. If Sandman operates as a contractor or mercenary group or is nation-state sponsored, the breadth of industries targeted will likely expand, especially with shifts in the political landscape, thereby broadening the threat landscape. The loss of confidentiality could cause a material impact on customers due to unauthorized access and exfiltration of sensitive information, leading to the loss of competitive advantage and intellectual property, potentially eroding market share and causing reputational damage.
These factors can have a cascading effect on financial performance as customers and partners lose trust, and the organization faces potential legal liabilities and regulatory fines. While there is no direct evidence of Sandman compromising the integrity and availability of data or systems, the exclusive risk to confidentiality alone can translate to significant financial repercussions. The realization of these risks and impacts underscores the critical need for implementing robust cybersecurity measures to safeguard sensitive information and maintain organizational trust.
3 APTs Conducted Cyber Espionage Against a Southeast Asian Government, Employing Sophisticated Tools and Techniques
Stately Taurus – Alloy Taurus – Gelsemium – Data Exfiltration – Cyber Espionage – Public Administration
Overview & Background
Several blog posts from Unit 42 detail a series of espionage attacks targeting a government in Southeast Asia, executed by separate threat actors grouped into three distinct clusters: CL-STA-0044, CL-STA-0045, and CL-STA-0046. These posts aim to provide details about each cluster’s operations, shedding light on the actors’ objectives, methods, and the vulnerabilities exploited. The analysis encompasses a variety of systems and data, including the identification of malicious software, network interactions, and the examination of compromised assets, to produce a holistic view of the threat landscape.
The three identified clusters of activity, CL-STA-0044, CL-STA-0045, and CL-STA-0046, represent distinct cyber-espionage campaigns attributed to different Advanced Persistent Threat (APT) groups. CL-STA-0044 is linked to Stately Taurus (Mustang Panda), a group known for its focus on intelligence collection, primarily targeting non-profit organizations and entities in the education sector across Southeast Asia. Alloy Taurus, associated with CL-STA-0045, has been observed conducting campaigns to establish long-term persistence and obtain access to telecommunications and technology companies, often exploiting vulnerabilities in web servers. CL-STA-0046 is suspected to be tied to the rarely-seen Gelsemium APT, a group with a history of sophisticated attacks against governmental institutions, utilizing various tools and techniques to maintain access and perform reconnaissance.
Threat Analysis
CL-STA-0044 (Stately Taurus/Mustang Panda)
The group meticulously scanned infected environments, identifying live hosts, open ports, domain users, and groups, utilizing tools like LadonGo, NBTScan, AdFind, and Impacket. They employed various credential-stealing techniques, deploying tools such as Hdump, MimiKatz, and DCSync and extracting the Ntds.dit file to access Active Directory data.
The group maintained access through multiple backdoors and web shells, notably using an undocumented variant of ToneShell malware, which is distinctive to Stately Taurus. This variant comprises three DLL components, each responsible for persistence, C2 communication, and executing commands. Additionally, the group deployed Cobalt Strike agents and ShadowPad backdoors, a modular malware associated with Chinese threat actors.
Stately Taurus demonstrated a high level of targeting precision, focusing on specific individuals within the victim organizations. They used the utility wevtutil to gather information about particular usernames and pinpoint hostnames of interest, which were later compromised. The group archived and exfiltrated numerous documents and sensitive information, utilizing tools like rar.exe and cloud storage sites, indicating a continuous intelligence-gathering operation.
Stately Taurus focused strategically on intelligence collection, primarily acquiring sensitive governmental information from Southeast Asia for political, economic, or strategic gains. The group demonstrated multifaceted objectives, including unauthorized access, data exfiltration, and establishing a persistent presence in targeted systems, mainly focusing on high-value individuals within organizations. Showcasing advanced technical proficiency, Stately Taurus employed a variety of distinctive tools and malware, such as an undocumented variant of ToneShell, Cobalt Strike, and ShadowPad, reflecting their adaptability, sophistication, and resourcefulness in conducting long-term operations.
CL-STA-0045 (Alloy Taurus/GALLIUM)
Initiated multi-wave intrusions, exploiting vulnerabilities in Exchange Servers to deploy numerous web shells. These shells facilitated the introduction of a variety of tools and malware, including China Chopper, Fscan, WebScan, Reshell, Zapoa, SoftEther VPN, Kerbrute, LsassUnhooker, GoDumpLsass, Mimikatz, LaZagne, Cobalt Strike, HTran, PuTTY, Quasar RAT, HDoor, Gh0stCringe RAT, and a variant of Winnti malware. The group demonstrated a mature approach, employing a combination of credential theft techniques, lateral movement strategies, and the installation of additional tools to maintain persistence and perform malicious activities.
In their operations, Alloy Taurus deployed a diverse array of tools and malware to achieve their objectives. Web shells, particularly China Chopper, were utilized for initial access and control. Scanners like Fscan and WebScan were employed for network scanning, while backdoors like Reshell and Zapoa facilitated remote command execution. The group also used SoftEther VPN software for establishing secure connections and bypassing security measures. They employed various credential theft tools to obtain domain credentials, including Kerbrute, LsassUnhooker, GoDumpLsass, Mimikatz, and LaZagne. For lateral movement across the network, AnyDesk was the tool of choice. Additional malware, including Cobalt Strike, Quasar RAT, HDoor, and Gh0stCringe RAT, were introduced for various malicious capabilities. The group also utilized tunneling tools such as HTran and PuTTY for SSH tunneling, and a variant of Winnti malware was deployed for additional capabilities.
Alloy Taurus is believed to operate with Chinese state interests, focusing on cyber espionage against government entities. The group’s intentions likely encompass long-term intelligence collection and establishing a resilient foothold within compromised networks for political, economic, or strategic advantage. The objectives involve targeting critical assets such as web servers and domain controllers, exploiting vulnerabilities, and exfiltrating sensitive information. Alloy Taurus demonstrates a high level of capabilities, utilizing a unique playbook of tools and malware, exhibiting a repetitive attack style, and effectively adapting to different environments and security measures.
CL-STA-0046 (Gelsemium)
Executed a series of stealthy and sophisticated activities over six months between 2022-2023, targeting sensitive IIS servers within a Southeast Asian government entity. The initial infection vector involved the installation of several web shells, including reGeorg, China Chopper, and AspxSpy, on a compromised web server, facilitating access, basic reconnaissance, lateral movement via SMB, and downloading additional tools. The attackers demonstrated adaptability by delivering new tools following unsuccessful installation attempts, highlighting their persistence and advanced capabilities.
The actors deployed a diverse set of additional tools and malware to further their control within the compromised environment. Among these were OwlProxy, a unique HTTP proxy with backdoor functionality previously used against the Taiwanese government, and SessionManager, a custom backdoor allowing command execution and communication with additional network systems. The use of Cobalt Strike, EarthWorm for creating a tunnel for C2 traffic, and SpoolFool, a local privilege escalation tool exploiting CVE-2022-21999, were also observed. These tools and others showcased the group’s adaptability, knowledge of diverse tools, and ability to leverage known vulnerabilities.
Gelsemium, operational since 2014, has a history of targeting diverse entities, including governments, universities, and manufacturers, primarily in East Asia and the Middle East. The group’s intentions for this operation were focused mainly on intelligence collection from government entities in Southeast Asia, reflecting a strategic interest in governmental operations and sensitive information. The objectives included gaining unauthorized access to sensitive IIS servers and exfiltrating valuable data, leveraging various tools and malware to maintain persistence and adaptability within the compromised environments. The capabilities of Gelsemium were evident in their use of rare and custom tools, adaptability to mitigation efforts, and the execution of a multifaceted and stealthy operation, indicative of a sophisticated and resourceful APT group.
Risk & Impact Assessment
The operations of clusters CL-STA-0044, CL-STA-0045, and CL-STA-0046 pose a significant threat to corporations, particularly regarding the confidentiality of sensitive and proprietary information. The detailed and covert intelligence-gathering activities and the utilization of advanced tools and techniques for unauthorized access highlight the potential for substantial impact on corporate entities and their assets. The compromise and potential disclosure of sensitive data jeopardize corporate competitive advantages and present a considerable risk of reputational damage, which could affect customer trust and market standing. While the exact impact on net sales, revenues, or income from continuing operations can be challenging to quantify, the strategic loss of proprietary information and the potential disruption of business operations emphasize the seriousness of the threat and its extensive ramifications for the corporate sector.
APT29 Phishing Campaigns Evolve Malware Delivery Methods Between March and July
APT29/Cozy Bear – ROOTSAW – Phishing – Phishing Links & Attachments – Public Administration
Overview & Background
The blog post from Mandiant titled “Backchannel Diplomacy: APT29’s Rapidly Evolving Diplomatic Phishing Operations” provides an in-depth examination of the evolving threat posed by APT29, a cyber-espionage group associated with the Russian government. The blog post highlights APT29’s latest tactics, techniques, and procedures (TTPs), focusing on their sophisticated phishing operations targeting diplomatic entities. By analyzing compromised communication channels, phishing emails, and malicious payloads, the blog post offers valuable insights into APT29’s modus operandi and its implications for diplomatic cybersecurity.
APT29, also known as Cozy Bear, is a highly sophisticated and well-resourced Advanced Persistent Threat (APT) group attributed to Russia’s Foreign Intelligence Service (SVR). The group has been active since 2008 and is known for its extensive cyber espionage campaigns targeting government networks, research institutes, think tanks, and various industries in Europe, the United States, and Asia. APT29 has been involved in several high-profile cyber attacks, including the 2016 Democratic National Committee (DNC) hack and the SolarWinds supply chain attack in 2020. The group uses a variety of tactics, techniques, and procedures (TTPs) to gain access to target networks, including spearphishing, social engineering, and the exploitation of software vulnerabilities. Once inside a network, APT29 deploys custom malware and tools to maintain persistence and exfiltrate sensitive data. The group is known for its advanced tradecraft, adaptability, and ability to blend into regular network traffic to evade detection. APT29 has a history of using trusted and legitimate cloud services for their attacks, such as social media platforms and cloud storage services. Overall, APT29 is considered one of the world’s most sophisticated and persistent APT groups, and its activities have been a significant concern for governments and organizations globally.
Threat Analysis
In response to Ukraine’s early planning and counteroffensive in June 2023, APT29 has been notably active, conducting phishing campaigns between March and July 2023 to gain initial access to targets, exhibiting a rapidly evolving approach. The group has demonstrated a shift in malware delivery methods, opting for more sophisticated and covert techniques to infiltrate their targets. The phishing emails sent by APT29 were meticulously crafted, often impersonating diplomatic entities, to lure the victims into interacting with malicious content. Various infection chains attributed to APT29 have coincided within a single campaign, suggesting that distinct initial access operators or subteams may be operating in parallel to service different regional targets or espionage objectives.
Decisions about which malware delivery approach to use or when to introduce new later-stage malware variants are unknown. However, mission-specific parameters such as targets or operational objectives may influence these decisions. Typically, APT29 reserves the first use of new capabilities for targets inside Ukraine or diplomatic entities associated with the North Atlantic Treaty Organization (NATO) or European Union (EU) member states. Then, these capabilities are incorporated into its broader operations with minimal changes, pointing to the group’s possible changing risk calculus after first exposure.
Throughout the phishing campaigns conducted from March to July 2023, APT29 exhibited a consistent pattern of evolution and adaptation in their malware delivery methods and tactics. In March, the group initiated campaigns using links, sometimes generated by URL shortening service, to direct victims to compromised websites hosting a new version of ROOTSAW with user-agent-based anti-analysis to filter out non-compatible victim devices. This approach was further refined in subsequent campaigns, shifting the anti-analysis guardrails server-side and introducing additional filtering layers, including IP filtering facilitated by public API services.
April saw a departure from using ROOTSAW and a shift towards using attachments, with victims directly receiving malicious ISO or ZIP files if they passed server-side checks, a tactic likely adopted to minimize forensic artifacts. The campaigns in May and June demonstrated a further evolution in delivery mechanisms, incorporating Scalable Vector Graphics (SVG) and introducing new variants of ROOTSAW, indicative of APT29’s continuous efforts to enhance their techniques. These months also witnessed a strategic balance between using actor-controlled servers and compromised websites, allowing for more controlled operations, including profiling victim information and delivering tailored next-stage downloaders. By July, they introduced ICEBEAT, a new downloader utilizing the Zulip messaging platform for C2, and the incorporation of ROOTSAW within PDFs marked a further evolution in APT29’s operations, showcasing their persistent pursuit of more sophisticated and covert infiltration methods.
APT29’s progression underscores their commitment to refining their techniques, ensuring the successful profiling of victims, and minimizing the risk of exposure and detection through the evolution in links and attachments, the variety in dropped files, and the strategic use of command and control servers.
APT29 has also made a concerted effort to update and evolve their later-stage malware, increasing the quantity and quality of tooling used across its campaigns. At least six distinct downloaders have been identified during the first half of 2023: BURNTBATTER, DONUT, SPICYBEAT, MUSKYBEAT, STATICNOISE, and DAVESHELL. BURNTBATTER is an in-memory loader observed loading the SPICYBEAT downloader through a shellcode dropper named DONUT, a public tool for creating position-independent shellcode. SPICYBEAT, written in C++, downloads the next-stage payload from DropBox or OneDrive. MUSKYBEAT is an in-memory dropper decoding and executing next-stage payloads. STATICNOISE, another downloader written in C, handles the final-stage payload. DAVESHELL, based on a publicly available repository, operates as an in-memory dropper using reflective injection to execute its embedded payload.
APT29’s intentions behind these sophisticated campaigns are multifaceted. Primarily, the group seeks to gain initial access to facilitate a centralized exploitation team’s collection of sensitive information, trade secrets, intellectual property, and government secrets for political, economic, or strategic advantage. The current targeting of diplomatic entities and government institutions indicates a focus on obtaining information concerning the current pivotal phase of the Ukraine/Russia war. The objectives of APT29 are clear: to infect systems from a diverse range of high-value targets with the ROOTSAW malware to deliver follow-on payloads. In terms of capabilities, APT29 is highly skilled and resourceful. The group’s ability to evolve their tactics, techniques, and procedures (TTPs), consistently update ROOTSAW, and use a diverse range of follow-on payloads showcases their advanced knowledge and skills in cyber espionage. The continuous adaptation and evolution demonstrate the significant resources available to them, making them a formidable threat to organizations worldwide.
Risk & Impact Assessment
Given the group’s sophisticated and evolving tactics to obtain unauthorized access to sensitive data and systems, there is a significant likelihood of losing confidentiality. The meticulously crafted phishing campaigns, the continuous adaptation of malware delivery mechanisms, and the targeting of high-value targets underscore the substantial risk of unauthorized access and disclosure of sensitive information. The impact of APT29’s operations on organizations could be considerable, potentially leading to a material impact on net sales, revenues, or income from continuing operations. The unauthorized access and likely exfiltration of proprietary information compromise the business operations of targeted organizations and could have cascading effects on revenue. The intentions behind APT29’s campaigns further amplify the potential damage, underscoring the imperative for robust cybersecurity measures to mitigate the risks and safeguard confidentiality.
SSH Fingerprint Leads to the Identification of Extensive Infrastructure Used in Ransomware Attacks
ShadowSyndicate – Ransomware – Cobalt Strike – IcedID – Matanbuchus – Sliver – Industries/All
Overview & Background
A blog post from Group-IB titled “Dusting for fingerprints: ShadowSyndicate, a new RaaS player?” provides an in-depth overview of the infrastructure leveraged by ShadowSyndicate, a potentially new and notable Ransomware-as-a-Service (RaaS) affiliate. The blog post aims to present preliminary conclusions about the group, offering insights into ShadowSyndicate’s infrastructure while leaving avenues for further research into the group’s identity open for exploration. Group-IB’s analysis focuses on SSH servers, all with the same SSH fingerprint, attributed to ShadowSyndicate, tools and malware identified, SSH server characteristics (like server owners and locations), and the SSH server’s links to various ransomware families.
Threat Analysis
In Group-IB’s report, they stated that it’s “incredibly rare for one Secure Shell (SSH) fingerprint to have such a complex web of connections with a large number of malicious servers.” Due to this rarity, Group-IB decided to track the use of this SSH fingerprint to a single threat actor, ShadowSyndicate. Every intelligence report aims to answer one or more questions. For Group-IB’s report, they ultimately sought to determine whether ShadowSyndicate is a hoster, DevOps engineer, a bulletproof hosting provider, an initial access broker, or a Ransomware-as-a-Service affiliate. Group-IB’s analysis points to ShadowSyndicate working as an affiliate for various Ransomware-as-a-Service (RaaS) operations. However, additional data and analysis are needed to confirm this hypothesis.
Group-IB’s detailed research reveals 85 servers have the same Secure Shell (SSH) fingerprint, with at least 52 servers used as a Cobalt Strike C2 framework. With high confidence, Group-IB attributed ShadowSyndicate to Quantum ransomware activity in September 2022, Nokoyawa ransomware activity in October and November 2022, and March 2023, as well as to ALPHV activity in February 2023. Group-IB attributed ShadowSyndicate to Royal, Cactus, and Play ransomware activity with low confidence.
ShadowSyndicate’s connection to CL0P is less conclusive. However, Group-IB’s research uncovered several potential links between ShadowSyndicate and Cl0p infrastructure. Several IP addresses attributed to Cl0p now use the ShadowSyndicate SSH key, suggesting a possible link to ShadowSyndicate. These servers are now used as C2 infrastructure for Cobalt Strike or Metasploit.
Group-IB also identified evidence that a small set of servers are being used as command and control (C2) servers or connected to Sliver. Sliver is an open-source penetration testing tool developed in the programming language Go. Like Cobalt Strike and Metasploit, Sliver can be used by threat actors in real-life attacks. Additionally, two servers have been linked to IcedID infection chains, leading to Quantum and Nokoyawa ransomware families. Group-IB also potentially identified two servers linked to Matanbuchus, a Malware-as-a-Service (MaaS) loader. Matanbuchus is used to execute .exe payloads and for loading and executing shellcodes and malicious DLL files. Finally, one server was detected as a Meterpreter C2 in March 2023.
Group-IB’s research also revealed that 18 entities own SSH servers linked to ShadowSyndicate. The following owners accounted for almost 50% of the total owners.
- Flyservers S.A.
- Channelnet
- Reliable Communications s.r.o.
- DATASOLUTIONS S.A.
- Alviva Holding Limited
The servers’ locations are based in 13 different territories, with Panama being their preferred country of choice, followed by Cyprus, Russia, Seychelles, and Costa Rica.
Risk & Impact Assessment
Organizations face a pronounced threat due to the loss of confidentiality and availability caused by ransomware attacks linked to ShadowSyndicate’s infrastructure. The likelihood of an incident occurring is elevated due to the group’s extensive infrastructure and association with various Ransomware-as-a-Service (RaaS) operations. The primary risks are the unauthorized access and disclosure of sensitive information and the encryption of sensitive data and systems, allowing threat actors to extort victims for financial gain.
The material impact of such risks on organizations is substantial. Ransomware operations can lead to significant service disruptions and access to critical information, affecting an organization’s mission and functions. The potential unauthorized access and disclosure of sensitive information and encryption of sensitive data and systems can have severe financial repercussions, resulting in the loss of net sales, revenues, or income from continuing operations. Moreover, the reputational damage incurred from such breaches can have long-lasting effects on an organization’s standing and customer trust.
Latest Additions to Data Leak Sites
Professional, Scientific, and Technical Services – Manufacturing – Information – Retail Trade – Real Estate and Rental and Leasing
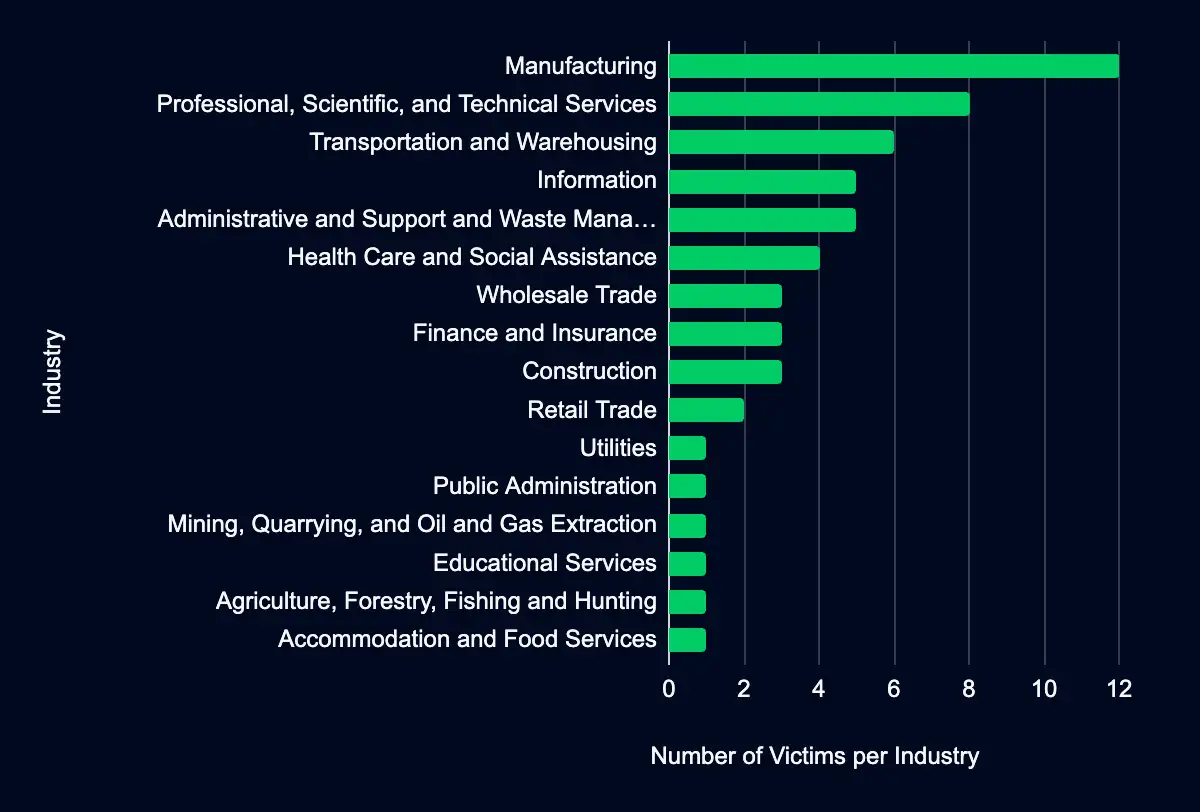
In the past week, monitored data extortion and ransomware threat groups added 57 victims to their leak sites. Of those listed, 30 are based in the US. Manufacturing was the most popular industry listed, with 12 victims. This industry is followed by eight in Professional, Scientific, and Technical Services, six in Transportation and Warehousing, five in Information, and Administrative and Support and Waste Management and Remediation Services.
CISA Adds 4 CVEs to its Known Exploited Vulnerabilities Catalog
Apple/CVE-2023-41991 – Apple/CVE-2023-41992 – Apple/CVE-2023-41993 – Trend Micro/CVE-2023-41179
Within the past week, CISA added four CVEs to the catalog, affecting products from Apple and Trend Micro. Threat actors can exploit these vulnerabilities for code execution, privilege escalation, or bypass signature validation. It is crucial to promptly apply updates or follow vendor instructions to mitigate these vulnerabilities, with CISA recommending mitigative action occur between 12 and 16 October 2023.
| CVE ID | Vendor/Project | Product | Description | CISA Due Date |
|---|---|---|---|---|
| CVE-2023-41991 | Apple | Multiple Products | Apple iOS, iPadOS, macOS, and watchOS contain an improper certificate validation vulnerability that can allow a malicious app to bypass signature validation. | 10/16/23 |
| CVE-2023-41992 | Apple | Multiple Product | Apple iOS, iPadOS, macOS, and watchOS contain an unspecified vulnerability that allows for local privilege escalation. | 10/16/23 |
| CVE-2023-41993 | Apple | Multiple Products | Apple iOS, iPadOS, macOS, and Safari WebKit contain an unspecified vulnerability that can allow an attacker to execute code when processing web content. | 10/16/23 |
| CVE-2023-41179 | Trend Micro | Apex One and Worry-Free Business Security | Trend Micro Apex One and Worry-Free Business Security contain an unspecified vulnerability in the third-party anti-virus uninstaller that could allow an attacker to manipulate the module to conduct remote code execution. An attacker must first obtain administrative console access on the target system in order to exploit this vulnerability. | 10/12/23 |
Let’s Secure Your Organization’s Future Together
At Deepwatch, we are committed to helping organizations like yours navigate the intricate world of cyber threats. Our cybersecurity solutions are designed to stay ahead of the curve, providing you with the proactive defenses needed to protect your organization from these threats.
Our team of cybersecurity professionals is ready to evaluate your systems, provide actionable insights, and implement robust security measures tailored to your needs.
Don’t wait for a cyber threat to disrupt your operations. Contact us today and take the first step towards a more secure future for your organization. Together, we can outsmart the threats and secure your networks.
What We Mean When We Say
Estimates of Likelihood
We use probabilistic language to reflect the Intel Team’s estimates of the likelihood of developments or events because analytical judgments are not certain. Terms like “probably,” “likely,” “very likely,” and “almost certainly” denote a higher than even chance. The terms “unlikely” and “remote” imply that an event has a lower than even chance of occurring; they do not imply that it will not. Terms like “might” reflect situations where we are unable to assess the likelihood, usually due to a lack of relevant information, which is sketchy or fragmented. Terms like “we can’t dismiss,” “we can’t rule out,” and “we can’t discount” refer to an unlikely, improbable, or distant event with significant consequences.
Confidence in Assessments
Our assessments and projections are based on data that varies in scope, quality, and source. As a result, we assign our assessments high, moderate, or low levels of confidence, as follows:
High confidence indicates that our decisions are based on reliable information and/or that the nature of the problem allows us to make a sound decision. However, a “high confidence” judgment is not a fact or a guarantee, and it still carries the risk of being incorrect.
Moderate confidence denotes that the information is credible and plausible, but not of high enough quality or sufficiently corroborated to warrant a higher level of assurance.
Low confidence indicates that the information’s credibility and/or plausibility are in doubt, that the information is too fragmented or poorly corroborated to make solid analytic inferences, or that we have serious concerns or problems with the sources.
Share