Executive Summary
A Proof-of-Concept (PoC) exploit code for a vulnerability tracked as CVE-2023-21716 in Microsoft Word’s RTF parser has been publicly released and shared on cybercrime forums. However, the PoC exploit code is not fully functional and only theoretically demonstrates remote code execution. Cybercriminals could modify the code to make it fully operational, and the initial threat vector could be through phishing emails with attached or linked weaponized Word .rtf documents. The vulnerability affects multiple versions of Microsoft Office, including Office 2007, Office 2010, Office 2013, Office 2016, and Office 365. Microsoft has released a security update to address the vulnerability and organizations should update their Microsoft Office software or apply the workarounds and be cautious of suspicious emails containing Word .rtf attachments.
Key Points
- PoC exploit code has been shared publicly and on cybercrime forums for a vulnerability tracked as CVE-2023-21716 in Microsoft Word’s RTF parser.
- The Publicly available PoC stops short of launching the Calculator app and theoretically demonstrates remote code execution, but will require modification to make the code fully functional.
- Cybercriminals will likely modify the code shared to make it fully operational, which will take time to test and operationalize.
- The vulnerability affects multiple versions of Microsoft Office, including Office 2007, Office 2010, Office 2013, Office 2016, and Office 365.
- Microsoft Office 2010 and later versions use Protected View, which requires an additional sandbox escape vulnerability to gain the victim’s privileges.
Introduction
Senior Security Engineer at Amazon and Metasploit contributor, Joshua Drake, posted a PoC Python script on his website, and Twitter, which has been shared on cybercrime forums for a vulnerability tracked as CVE-2023-21716 in Microsoft Word’s RTF parser that could allow cybercriminals to execute remote code without authentication using a weaponized RTF document. The security researcher designed the PoC to trigger the heap corruption issue to launch the Calculator app. However, the PoC stops short of launching the Calculator app to demonstrate code execution.
The vulnerability is triggered when the parser encounters a font table with excessive fonts, causing heap corruption. The vulnerability affects multiple versions of Microsoft Office, including Office 2007, 2010, 2013, 2016, and Office 365. However, Office 2010 and later versions use Protected View, which limits the damage caused by malicious documents obtained from untrusted sources. Microsoft released a security update in February 2023 to address it. It is essential to note that even a .rtf file renamed as a .doc extension can still reach the vulnerable code, making the vulnerability particularly dangerous.
Overview
In November 2022, Senior Security Engineer at Amazon and Metasploit contributor, Joshua Drake, submitted a vulnerability report to Microsoft, which details a heap corruption vulnerability found in Microsoft Word’s RTF parser, which was assigned CVE-2023-21716. If the vulnerability is triggered, cybercriminals can achieve remote code execution with the victim’s privileges without prior authentication. Cybercriminals can simply send a malicious RTF file containing an excessive number of fonts in the font table (\fonttbl) to the victim via email.
The RTF parser in Microsoft Word contains the heap corruption vulnerability, specifically when dealing with a font table with excessive fonts. The vulnerability affects Microsoft Office 2007, 2010, 2013, 2016, and Microsoft Office 365. However, Microsoft Office 2010 and later versions use Protected View, which can limit the damage caused by malicious documents procured from untrusted sources. Protected View is in effect when this vulnerability manifests, so a cybercriminal would require an additional sandbox escape vulnerability to gain full privileges. Microsoft released a security update to address this vulnerability as part of its Patch Tuesday February update.
On 5 March, Drake posted his vulnerability report to his website (qoop.org) along with a proof-of-concept (PoC) Python script that generates a file that triggers the vulnerability. He also posted a one-line PoC for CVE-2023-21716 to his Twitter account. The PoC posted on qoop.org was shared on the XSS forum by the user Weaver, who has a high reputation score of 9/10, on 6 March 2023. It is worth noting that changing the extension from .rtf to .doc extension can still reach the vulnerable code. The security researcher designed the PoC to trigger the heap corruption problem to launch the Calculator app. However, the PoC stops short of launching the Calculator app to demonstrate code execution.
Analyst Comment
Even though the PoC code is only theoretical, with the code shared on cybercriminal forums by users with high reputation scores, cybercriminals may modify the code shared to make it fully operational, which will take time to test and operationalize. However, it is possible that some cybercriminals will not take the time to operationalize the exploit code because a sandbox escape vulnerability is needed to exploit Office 2010 and later versions. Multiple open sources mention that the initial threat vector could be through phishing emails with attachments or links to weaponized Word .rtf documents.
Deepwatch’s Response
The Adversary Tactics and Intelligence team’s internal SOP and processes have been updated to identify unusual child processes launched by Office products. In addition, The Adversary Tactics and Intelligence threat research team detonated the Proof-of-concept (POC) exploit code in a controlled lab environment to identify any detection opportunities, which ATI will further test and, if appropriate, Deepwatch will include these opportunities in our detection library.
Be On the Lookout (BOLO)
- Microsoft Office executables such as WINWORD.exe spawning rare child processes like cmd.exe or powershell.exe
- Events with EventCodes 1001 or 1000 relating to “wwlib.dll” and “winword.exe” (Figures 1 & 2)
- These event codes are not necessarily indicative of exploit but can be used in hunting when correlated with 4688 command line data containing “winword.exe” and a .rtf file (or .rtf file renamed as .doc))
- WINWORD.exe launching .RTF files in the downloads or %temp% directories that may have originated from a phishing email (4688 Process Command Line or EDR process data, Figure 3)
- .RTF documents in email attachments from external/untrusted sources
- Note that open-source reporting indicates the file can be renamed with a .doc extension and still achieve the same end result. It is recommended to follow the actions in the recommendations section to prevent any current/future variations of this exploit
- .RTF files may be contained within popular container file types commonly used in phishing campaigns such as .zip or .iso

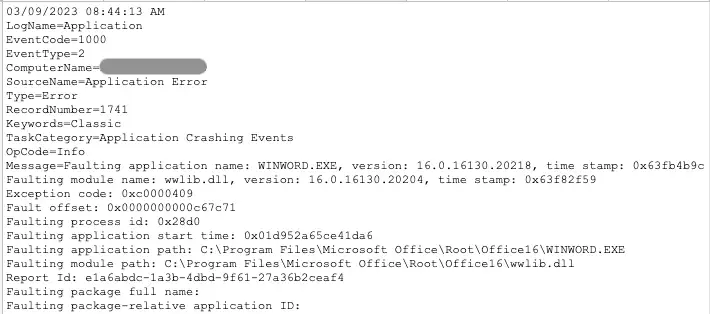
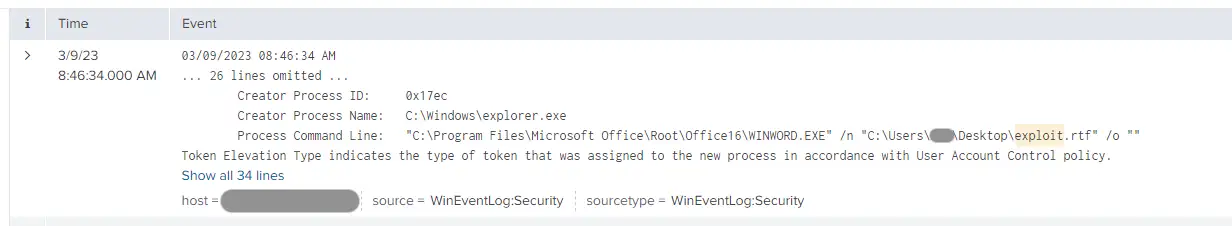
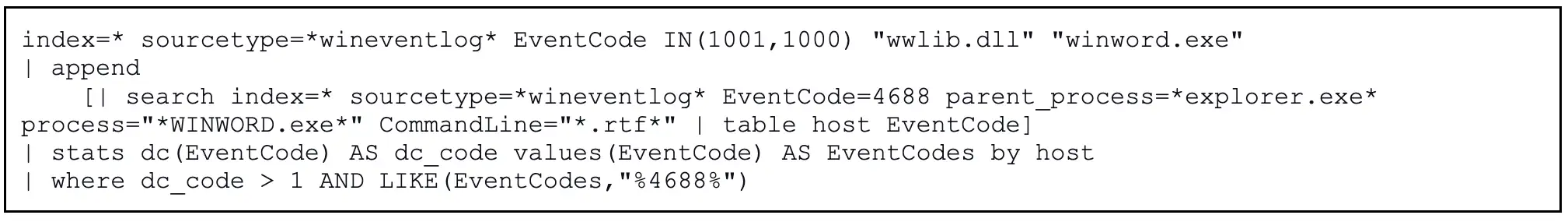
The Splunk query below identifies hosts presenting both 4688 process logs showing WINWORD.exe opening a .RTF file and corresponding crash logs relating to both WINWORD.exe and wwlib.dll. Note this is a statistics-driven approach and findings may warrant additional review to confirm validity.
Recommendations
Deepwatch recommends organizations update to the latest version. For those that are unable to update to the latest version, Microsoft has provided the following workarounds:
- Use Microsoft Office File Block policy to prevent Office from opening RTF documents from unknown or untrusted sources by following Microsoft’s guidance available here.
Sources
- CVE – CVE-2023-21716. (2022, December 13). cve.mitre.org; MITRE. https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2023-21716
- Drake, J. J. (2023, March 5). Microsoft Word RTF Font Table Heap Corruption. qoop.org. Retrieved March 9, 2023, from https://qoop.org/publications/cve-2023-21716-rtf-fonttbl.md
- Drake, J. (2023, March 5). https://twitter.com/jduck/status/1632471544935923712?s=20. Twitter. https://twitter.com/jduck/status/1632471544935923712?s=20
- Security Update Guide – Microsoft Security Response Center. (n.d.). msrc.microsoft.com. Retrieved March 9, 2023, from https://msrc.microsoft.com/update-guide/vulnerability/CVE-2023-21716
- Drake, J. (n.d.). LinedIn Profile. linkedIn.com; LinkedIn. Retrieved March 9, 2023, from https://www.linkedin.com/in/jduck1337/
Share