November 15, 2021
Prepared by Deepwatch Threat Intel Team
Key Points:
- Palo Alto Networks GlobalProtect VPN has a new zero-day vulnerability, identified as CVE-2021-3064, affecting PAN-OS 8.1 versions before PAN-OS 8.1.17.
- This vulnerability allows for unauthenticated, remote code execution on vulnerable systems.
- Deepwatch Threat Intel Team assesses with high confidence that a publicly available exploit is highly likely to surface.
- Deepwatch advises vulnerable organizations to install the PAN updates. PAN has also released Threat Prevention signatures 91820 and 91855, which may be used to prevent exploitation as enterprises prepare for the software upgrade.
Summary:
Palo Alto Networks GlobalProtect VPN has a new zero-day vulnerability that an unauthenticated network-based attacker may exploit to execute arbitrary code with root user rights on affected devices.
The security flaw is identified as CVE-2021-3064 (CVSS score: 9.8) and affects PAN-OS 8.1 versions before PAN-OS 8.1.17. Randori, a cybersecurity company, located in Massachusetts, is credited with detecting and reporting the zero-day. This vulnerability allows for unauthenticated, remote code execution on susceptible product installations. Randori has discovered over 10,000 vulnerable instances on internet-facing assets.
Randori stated that “CVE-2021-3064 is a buffer overflow that occurs while parsing user-supplied input into a fixed-length location on the stack. The problematic code is not reachable externally without utilizing an HTTP smuggling technique. Exploitation of these together yields remote code execution under the privileges of the affected component on the firewall device. The smuggling capability was not designated a CVE identifier as it is not considered a security boundary by the affected vendor.”
Randori’s Attack Team created a reliable, functional exploit and used it as part of its continuous and automated red team platform. Randori’s team was able to take control of the target, access essential configuration data, and extract passwords, among other things. After gaining control of the firewall, an attacker will have sight into the internal network and will be able to move laterally.
According to the timeline posted to Randori’s zero-day notification, the vulnerability was first identified on November 19, 2020, and started using the exploit chain on December 1, 2020, as part of their continuous and automated red team platform.
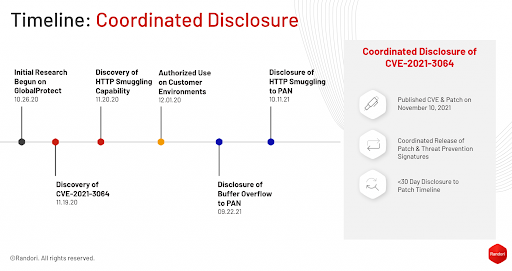
Source: Randori
The Randori Attack team was able to exploit the following systems with GlobalProtect enabled and accessible successfully:
- Palo Alto Networks PA-5220
- PAN-OS 8.1.16
- ASLR enabled in firmware for this device
- Palo Alto Networks PA-VM
- PAN-OS 8.1.15
- ASLR disabled in firmware for this device
Randori has stated on their disclosure notice that “Detailed technical information usually appearing in our attacker’s notes is not provided at this time to allow a period for customers of the affected vendor to patch or upgrade their systems. We will be releasing technical details on December 10, 2021 and hosting a live webinar breaking down the technical details of the exploit on December 14, 2021. Follow @RandoriAttack on Twitter for updates.”
Deepwatch Threat Intelligence Outlook:
Deepwatch Threat Intel Team assesses with high confidence that a publicly available exploit is highly likely to surface as threat actors are interested in accessible gateways into organizations, primarily through VPN gateway devices. Deepwatch advises organizations using PAN-OS 8.1 versions before PAN-OS 8.1.17 to install the Palo Alto Networks updates. Palo Alto has also released Threat Prevention signatures 91820 and 91855, which may be used to prevent exploitation as enterprises prepare for the software upgrade.
↑
Share